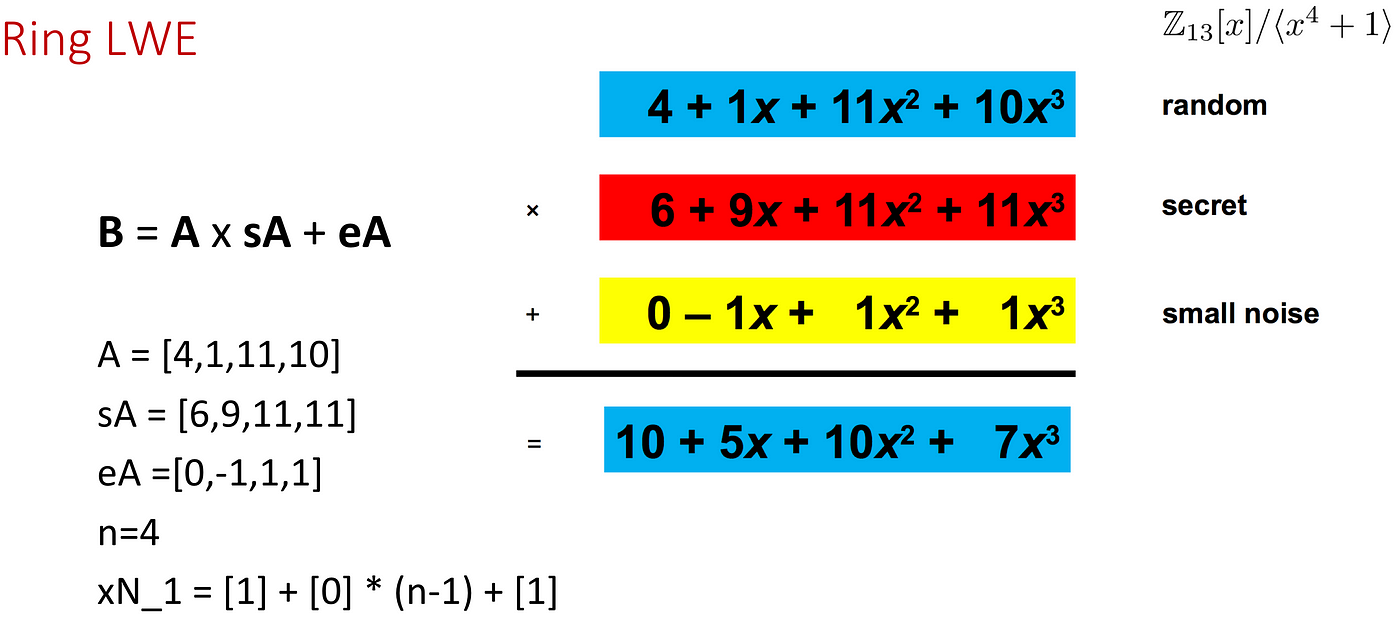
Learning With Errors and Ring Learning With Errors | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

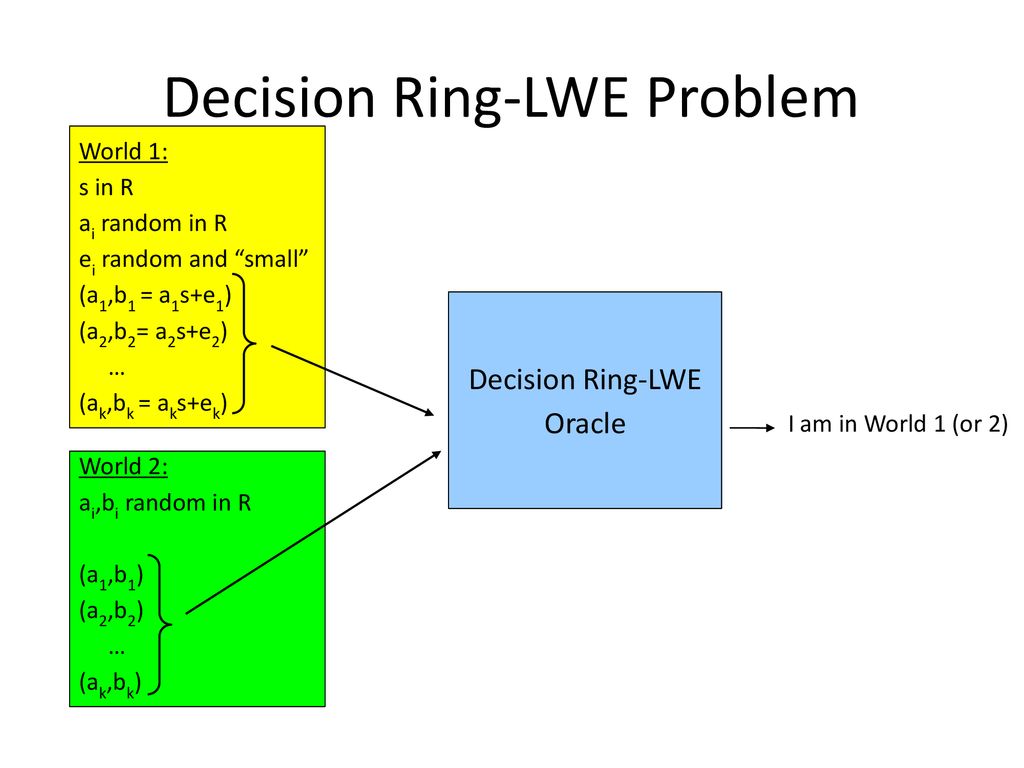
Directions in Practical Lattice Cryptography Vadim Lyubashevsky IBM Research – Zurich. - ppt download

Learning With Errors and Ring Learning With Errors | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
GitHub - CMMayer/Toolkit-for-Ring-LWE-v1.0: Implementation of a toolkit for ring-LWE based cryptography in arbitrary cyclotomic number fields.







![The ring-LWE-based LNV scheme [9]. | Download Scientific Diagram The ring-LWE-based LNV scheme [9]. | Download Scientific Diagram](https://www.researchgate.net/publication/343770789/figure/fig1/AS:1041867634393090@1625412009383/The-ring-LWE-based-LNV-scheme-9.png)

![PDF] Module-LWE versus Ring-LWE, Revisited | Semantic Scholar PDF] Module-LWE versus Ring-LWE, Revisited | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7f0b73dcb090e90962042ef64cd1d162893cfff7/3-Figure1-1.png)