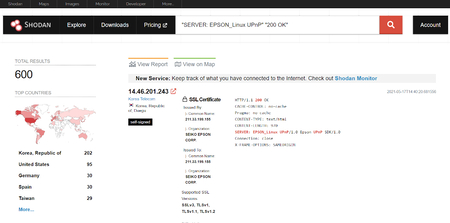
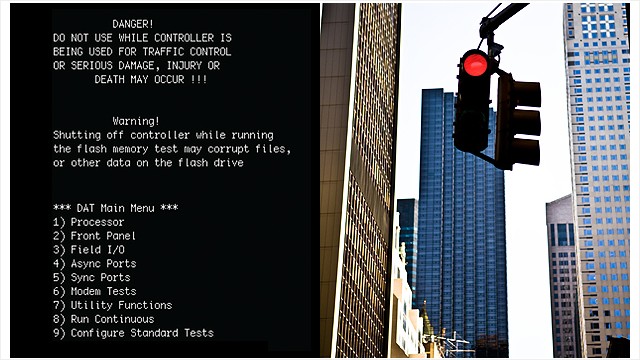
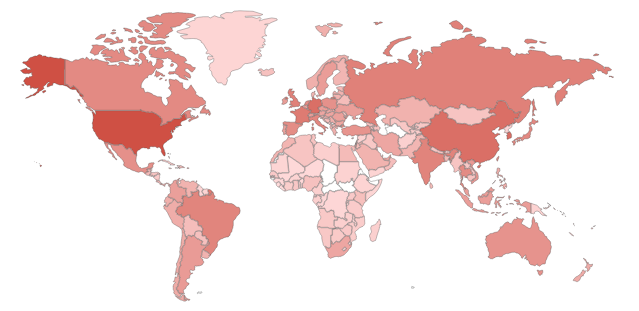
Shodan on Twitter: "Good news: Telnet use is in steady decline - https://t.co/8IsuWEDS1m https://t.co/FFxvt7RyJv" / Twitter

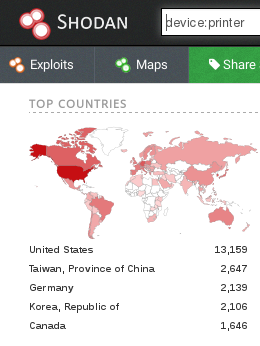
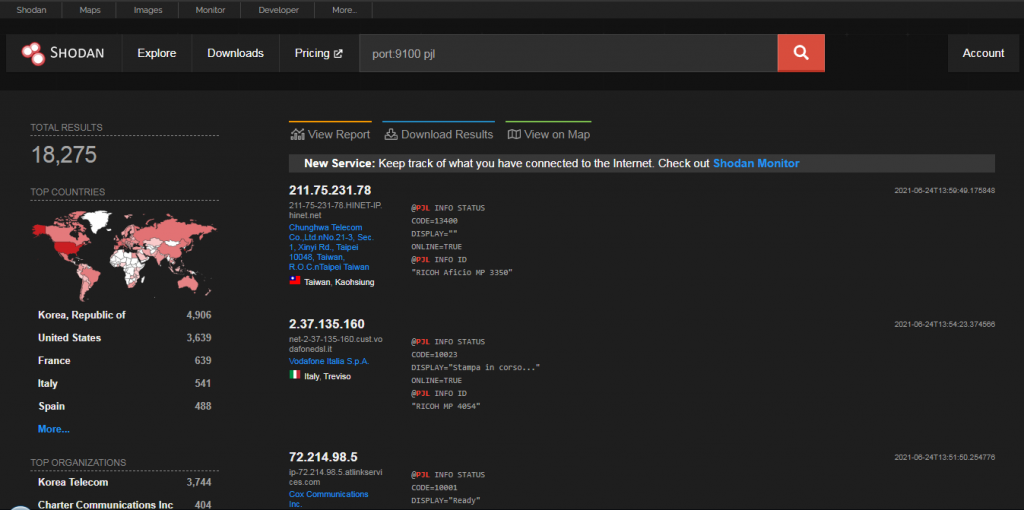
Shodan on Twitter: "Shodan knows you need new toner (and which printers people use the most): http://t.co/pFwro6VnDi http://t.co/kLnnLRREep" / Twitter
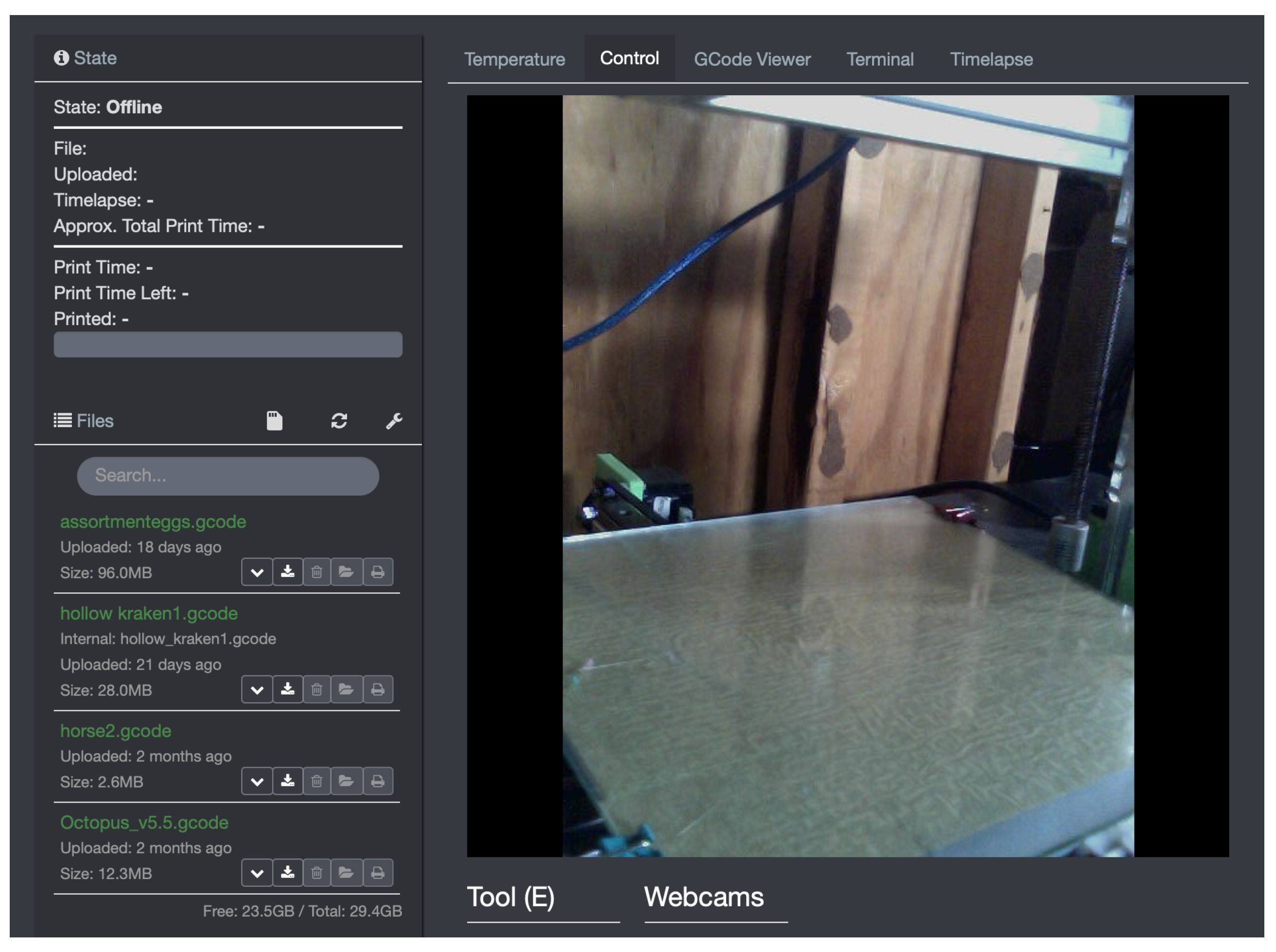
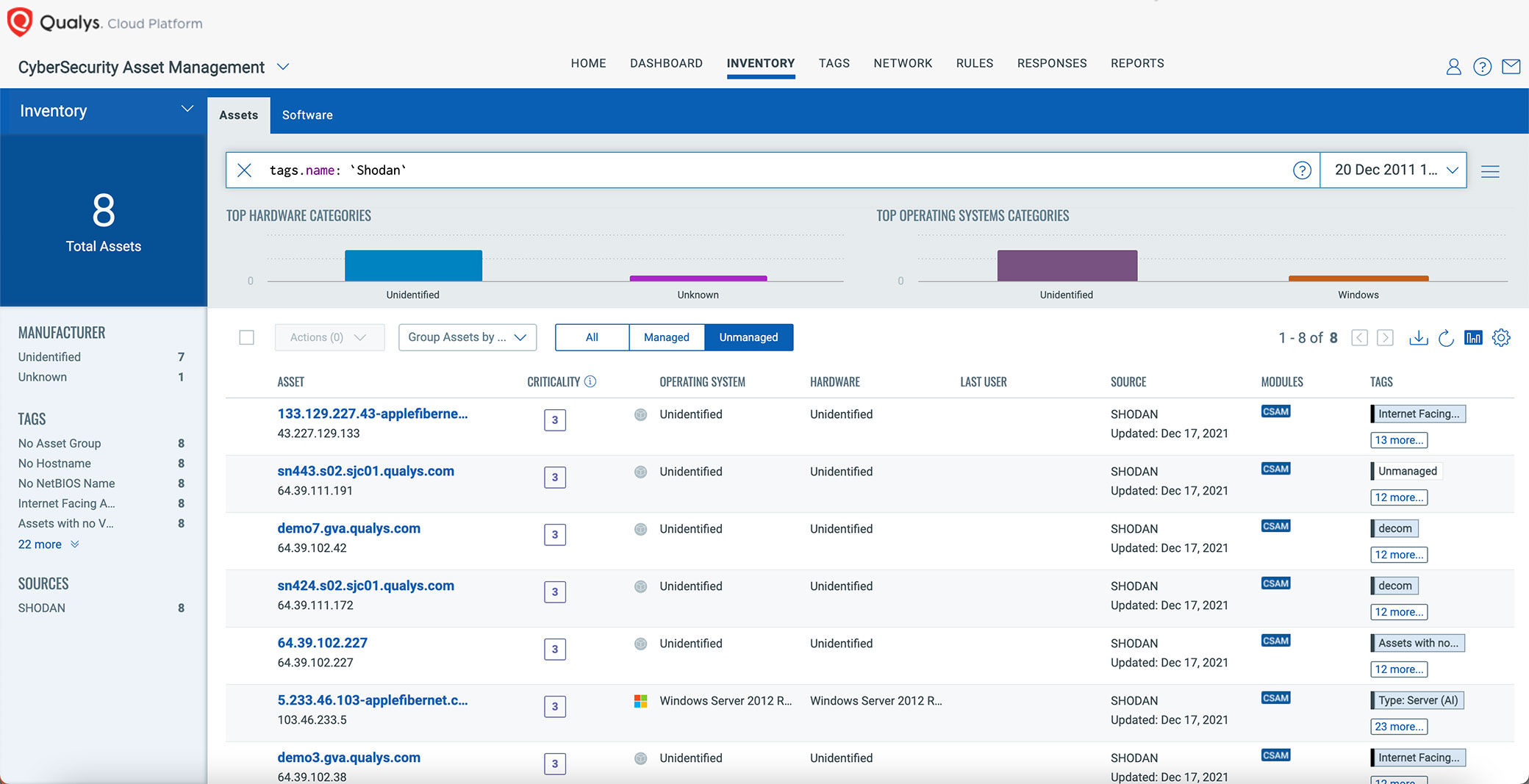
Applied Sciences | Free Full-Text | Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era
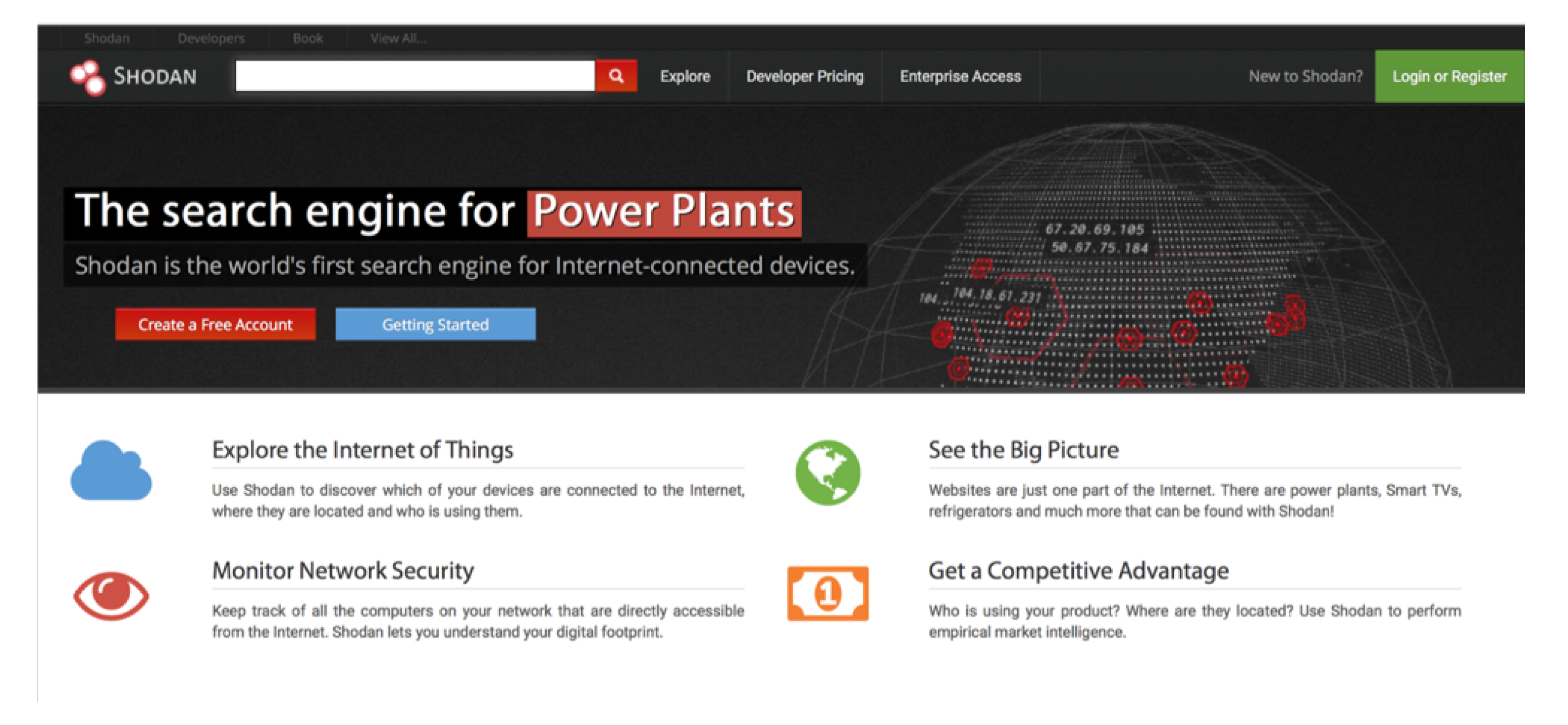












![Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle] Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/shodan/s_hero2x?1620485817)